what exploits are online the cybersecurity threat you need to know Cybersecurity threats and attacks: all you need to know
If you are looking for Cybersecurity Threats and Attacks: All You Need to Know you've visit to the right place. We have 25 Images about Cybersecurity Threats and Attacks: All You Need to Know like Cybersecurity Threats and Attacks: All You Need to Know, What is a Cybersecurity Exploit? 5 Dangerous Types You Need to Know and also Types of Cyber Security Threats | NEIT. Read more:
Cybersecurity Threats And Attacks: All You Need To Know
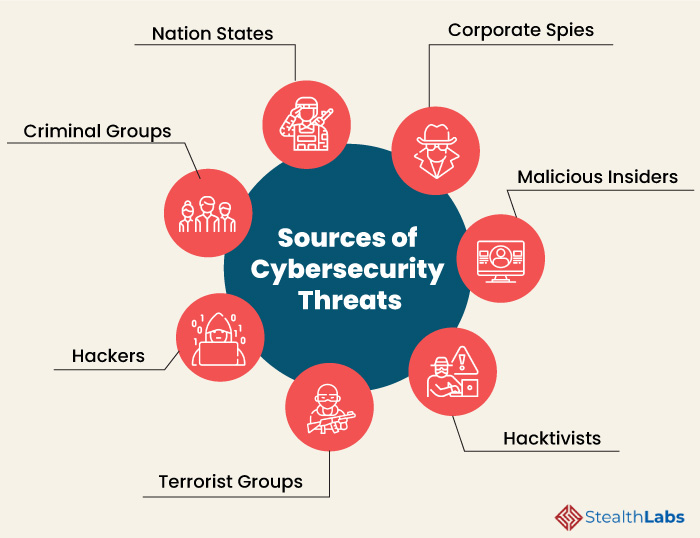 www.stealthlabs.com
www.stealthlabs.com
Cybersecurity Threats and Attacks: All You Need to Know
Cyber Security Presentation
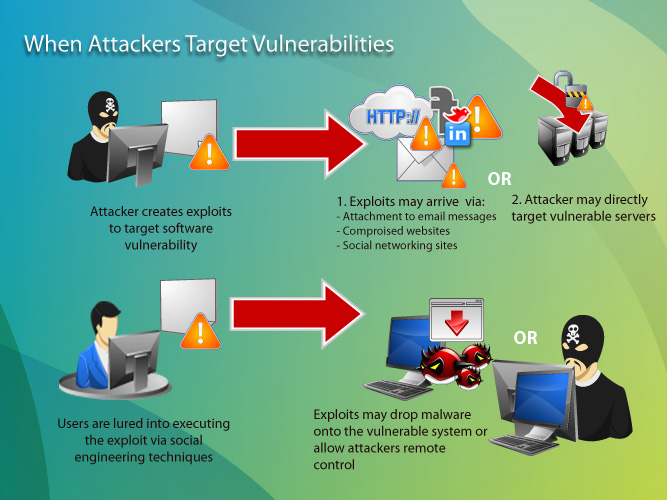 www.slidemake.com
www.slidemake.com
Cyber Security Presentation
What Do You Need To Know About Cybersecurity Exploits
 medium.com
medium.com
What Do You Need To Know About Cybersecurity Exploits ...
9 Top Cloud Threat Detection (CTR) Tools - Spectral
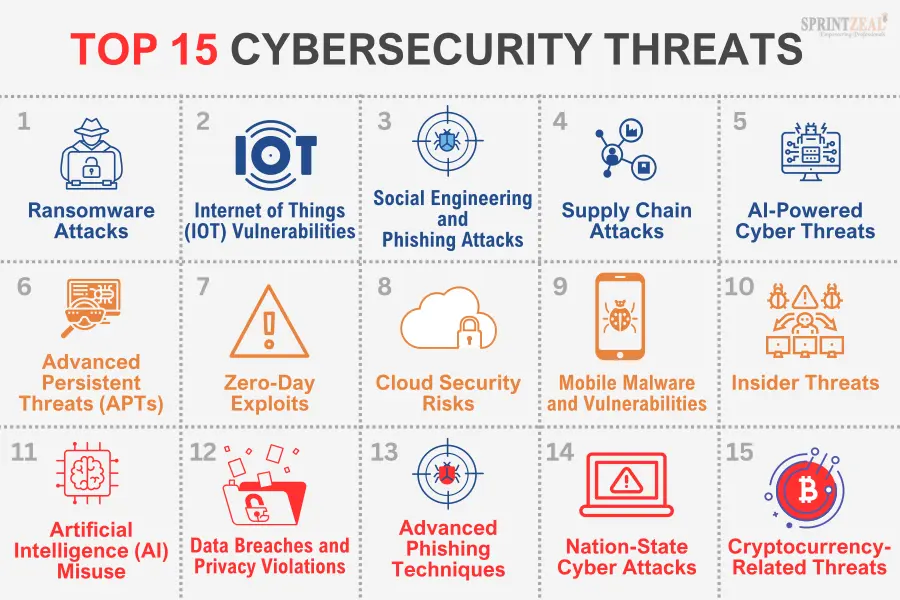 spectralops.io
spectralops.io
9 Top Cloud Threat Detection (CTR) Tools - Spectral
Understanding The Impact Of Cyber Threats - CyberMatters
 cybermatters.info
cybermatters.info
Understanding the Impact of Cyber Threats - CyberMatters
Cybersecurity Threats: What You Need To Know - WEBitronix
 webitronix.com
webitronix.com
Cybersecurity Threats: What You Need to Know - WEBitronix
What Is Cyber Threat Intelligence (CTI)? | Xcitium
 www.xcitium.com
www.xcitium.com
What is Cyber Threat Intelligence (CTI)? | Xcitium
10 Most Common Cybersecurity Vulnerabilities | CyberGhost VPN
10 Most Common Cybersecurity Vulnerabilities | CyberGhost VPN
What Is Exploit And How To Protect Your Computer?
 www.wallarm.com
www.wallarm.com
What is Exploit and How to Protect Your Computer?
The Growing Threat Of Cyber Crime Exploiting System Vulnerabilities
 medium.com
medium.com
The Growing Threat of Cyber Crime Exploiting System Vulnerabilities ...
Cyber Attack Types
 mavink.com
mavink.com
Cyber Attack Types
The 7 Layers Of Cyber Security : Attacks On OSI Model
 iso-27001-journey.blogspot.com
iso-27001-journey.blogspot.com
The 7 Layers of Cyber Security : Attacks on OSI model
The Most Exploited Cyber Security Vulnerabilities | IT Pro
 www.itpro.com
www.itpro.com
The most exploited cyber security vulnerabilities | IT Pro
Cybersecurity Threats And Attacks: All You Need To Know
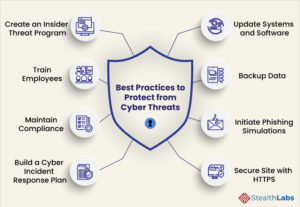 www.stealthlabs.com
www.stealthlabs.com
Cybersecurity Threats and Attacks: All You Need to Know
What Is Phishing? Know Everything About The Top 15 Cyber Security
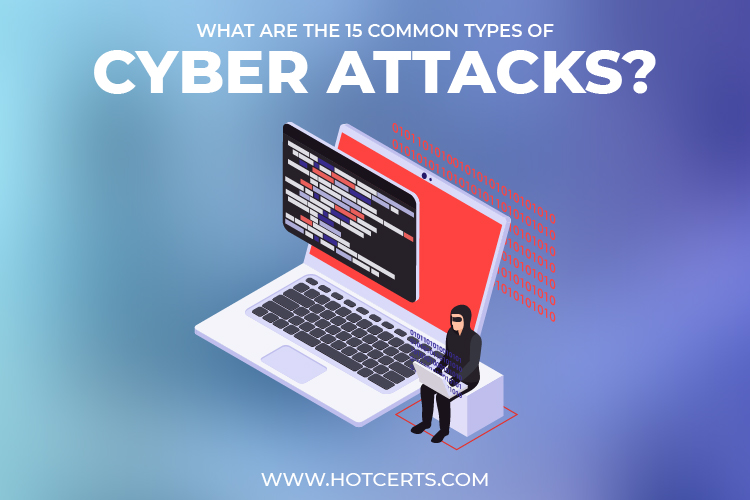 hotcerts.com
hotcerts.com
What is Phishing? Know Everything About the Top 15 Cyber Security ...
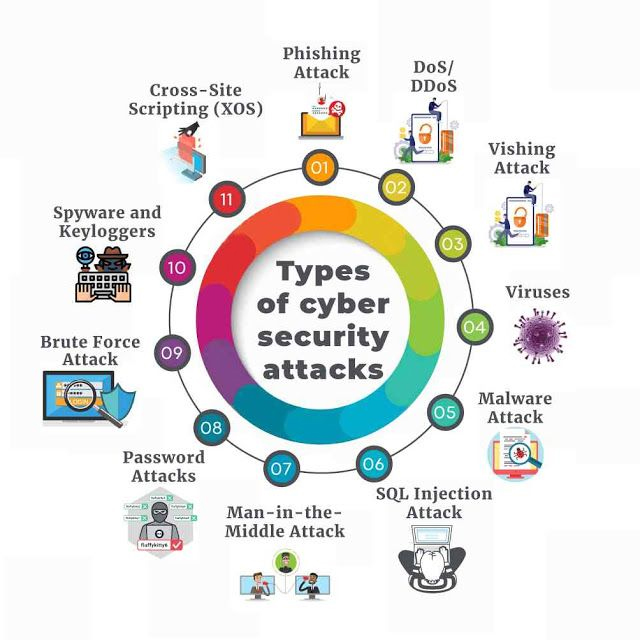
Types Of Cybersecurity Attacks And How To Prevent Them
 www.mygreatlearning.com
www.mygreatlearning.com
Types of Cybersecurity Attacks and How to Prevent Them
Cyber Threats Come In A Variety Of Shapes And Sizes.
 www.biovustechnologies.com
www.biovustechnologies.com
Cyber threats come in a variety of shapes and sizes.
Cybersecurity Threats And Attacks: All You Need To Know
 www.stealthlabs.com
www.stealthlabs.com
Cybersecurity Threats and Attacks: All You Need to Know
DocsAllOver | Understanding The Basics: Types Of Cyber Threats & Attacks
 docsallover.com
docsallover.com
DocsAllOver | Understanding the Basics: Types of Cyber Threats & Attacks
Top Cybersecurity Threats. What You Need To Know
 globalowls.com
globalowls.com
Top Cybersecurity Threats. What You Need to Know
Must Know Online Threats And Prevention Tips | WAZILE Inc.
 www.wazile.com
www.wazile.com
Must Know Online Threats and Prevention Tips | WAZILE Inc.
Types Of Cyber Security Threats | NEIT
 www.neit.edu
www.neit.edu
Types of Cyber Security Threats | NEIT
What Is A Cybersecurity Exploit? 5 Dangerous Types You Need To Know
 texmg.com
texmg.com
What is a Cybersecurity Exploit? 5 Dangerous Types You Need to Know
Cybersecurity Threats And Attacks: All You Need To Know
 www.stealthlabs.com
www.stealthlabs.com
Cybersecurity Threats and Attacks: All You Need to Know
Protecting Yourself Online: Best Practices And Strategies
 yourtechnologyboy.blogspot.com
yourtechnologyboy.blogspot.com
Protecting Yourself Online: Best Practices and Strategies
Cyber attack types. Cyber threats come in a variety of shapes and sizes.. What do you need to know about cybersecurity exploits ...